A new trend has emerged from the COVID-19 pandemic — that of opportunistic cybercriminals preying on Internet users looking to stay informed on the latest coronavirus updates.
In the first quarter of 2020, Google’s Safe Browsing service recorded a steady increase in the number of phishing sites — websites set up to trick people into handing over personal information — peaking at nearly 51,000, the highest number recorded since November 2017. Many of these can be attributed to the thousands of new coronavirus website domains registered since the start of the year.
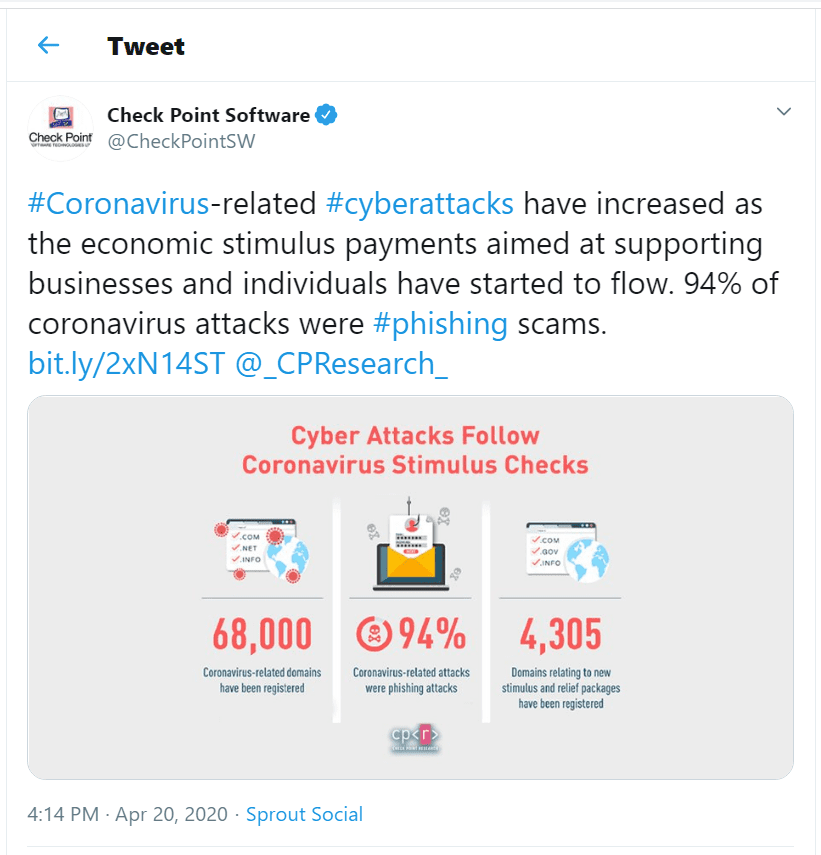
Similarly, there has been a spike in phishing emails with some researchers recording a 667% increase since the end of February alone.
These forms of malicious activities, often done hand-in-hand, are admittedly not new and nor are our efforts to mitigate them. So you may read the post below and think “I’ve heard this all before”. And that’s because you probably have!
However, cybersecurity and information security professionals, just like health professionals, will tell you how important it is to repeat the message multiple times (many times ad nauseam) to make it stick.
For as we’ve always known, and now come to truly understand, taking the time to wash our hands for at least 20 seconds can go a long way to reducing the risk of becoming sick or spreading germs and viruses.
Please share this post with your colleagues, your family, and friends to help them help all of us.
Tips to spot phishing scams
Phishing and spam are often grouped together as junk mail. Though both of them are equally annoying and unwanted, their purposes are very different.
Spam emails seek to promote and sell a product to as many people as possible. In contrast, phishing emails are expressly designed to obtain personal information (personal identity card information, banking details like debit and credit card information, passwords, account IDs, and so forth), which can then be used to access targeted financial and other important accounts. Incredibly, 91% of cyber attacks now start with a phishing email.
Most COVID-19 related phishing campaigns are using one or a combination of tactics. These include:
- Email Phishing (as above) and Spear Phishing, where attackers send unsolicited emails from a known or trusted sender in order to induce targeted individuals to reveal confidential information.
- Domain spoofing — attackers build a website similar to a legitimate website including its URL and email domain.
- Vishing and Smishing — phishing over phone calls and SMS
- Angler Phishing, which involves attackers masquerading as a customer service account on social media, hoping to reach a disgruntled consumer.
- Phishing via HTTPS (that lock in your address bar doesn’t keep you safe from phishers). 58% of phishing websites are now served via HTTPS.
No wonder there is a new ransomware named CovidLock as hackers are known to use every single opportunity to exploit unpredictable times and vulnerabilities associated to them. There are even some legitimate companies that are committing data privacy breaches without our knowledge and consent and without knowing how important our information is, we won’t take any action. One of the example is well known social media giant whose new feature, which monitors and tracks what you do when you’re offline and not on the social media platform. It records every website you’ve visited and apps you have used including online banking. However you can turn off this feature from settings.
There’s also a growing number of more sophisticated campaigns being uncovered too, which include regionally-specific details trying to trick recipients into clicking a malicious link.

The case shown in the tweet above demonstrates that if a recipient clicks on the Safety Measures link, it brings them to a spoofed World Health Organization (WHO) website, which prompts them for their email address and password. Unsurprisingly, WHO has already given guidelines warning people about cybercriminals who pretend to be WHO.
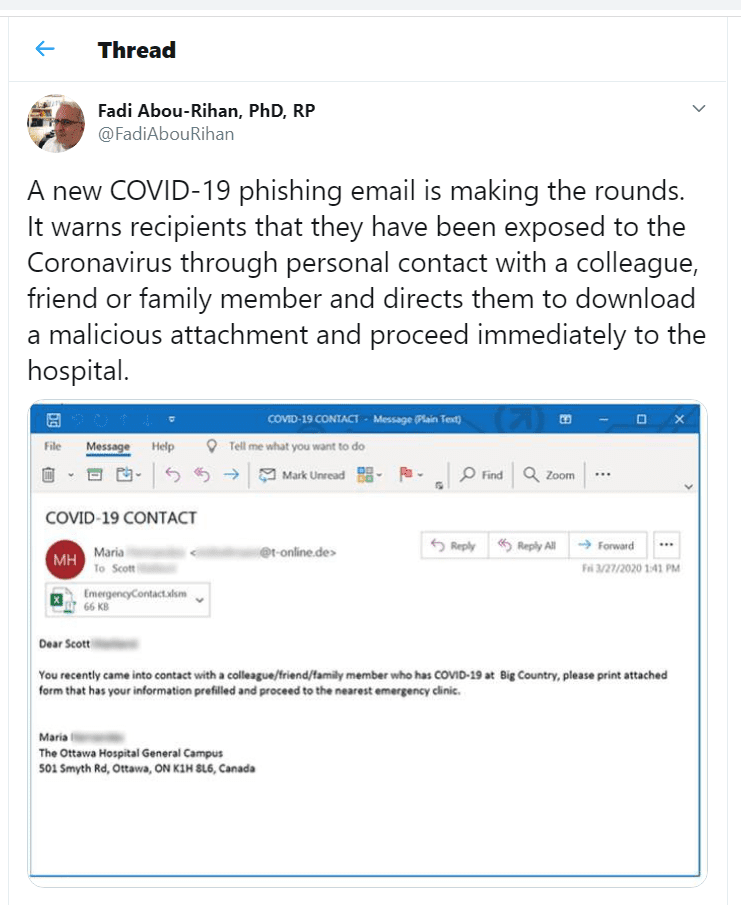
Similarly in the following example, the downloadable file, which is made out to be from a local hospital, is malicious. Even Android user are also affected by Covid -19 themed attacks that is a fake real-time coronavirus tracking Android app, called “COVID19 Tracker,” was found to abuse user permissions to change the phone’s lock screen password and install CovidLock ransomware in return for a $100 bitcoin ransom.
Here are some ways to determine whether you are dealing with a scammer or a legitimate merchant.
- Always check the sender’s email address. Be careful if the sender is using a public email domain (for example, @gmail.com or @yahoo.com).
- Watch out for spelling and/or grammatical errors in urls. For example www.mochacoffee.com vs. www.rnochacoffee.com. The same goes for email domains.
- Use generic salutations such as “Dear valued member,” “Dear account holder,” or “Dear customer.”
- If you receive a suspicious email, do not click the links or download the attachments, it may infect your device.
Filter, report, and share
Email filters are a great way to help you manage and protect yourself from malicious emails. That said, the details that some malicious actors add to their emails (including the sender email address) can sometimes be misinterpreted as a valid email, which is why you should always be cautious of any suspicious messages.
As security is every user’s business, it’s also worth sharing such suspicious messages with your security teams of your email provider, so they can add it to their filter list.
If you use Outlook, follow the steps below to help Microsoft update its filters quicker.
- Compose a new email.
- Enter [email protected] or [email protected] in the ‘To’ field.
- Add the junk/spam or phishing email as an attachment.
- Enter the subject of the junk or phishing email.
- Click send.
- Move the email to junk.
For Gmail, click the three dots at the top-right corner, then ‘Report Phishing’, or ‘Report Spam’ as appropriate.
Alternatively, you can send the email to the Anti-Phishing Working Group at [email protected] — they will include the example in reports they compile and share it with security groups and organizations all around the world, including Computer Emergency Response Teams, which help protect more users.
In the end, I would like to salute all the organizations and individuals who are front line warriors against Cyber Attacks. I would particularly want to appreciate efforts of Internet Society, Internet Corporation for Assigned Names and Numbers (ICANN), Asia Pacific Network Information Centre (APNIC) for creating awareness among masses and their efforts in ensuring safer browsing.
Acknowledgements: Thanks to Robbie Mitchell (Asia Pacific Network Information Centre), Muhammmad Imran Khan and Saeid Rezaei (University College Cork – National University of Ireland), Hassan Ali Shah (Electronic Certification and Accreditation Council, Pakistan), Madeeha Saeed (PMAS-Arid Agriculture University Rawalpindi, Pakistan), Mariyam Zaheer (Colorado Governor’s Office of Information Technology, USA) and Aisha Arshad (NED University of Engineering and Technology, Pakistan) for their inputs.
Muhammad Farhan Khan is a Doctoral Researcher under the supervision of Professor Dr. Dirk Pesch, at the School of Computer Science & IT, University College Cork – National University of Ireland and Confirm SFI Smart Manufacturing Research Centre, Ireland. He is the former General Secretary of Internet Society Pakistan Islamabad Chapter.







